The Firebox NV5 – A Different Firewall Appliance
We are pleased to announce the release of a new tabletop firewall appliance. With the release of the Firebox NV5, network administrators can quickly and affordably deploy multiple remote devices or small offices. Why a Firebox NV5 firewall? The WatchGuard NV5 is the perfect solution for remote applications that require management access or secured traffic. …
The 4 most Effective steps to mitigate Account Theft
The migration of means to the Cloud has been the common denominator in company business strategies over the last two years, coupled with the rising number of incidents involving the theft of sensitive information and user passwords on Cloud platforms. According to the Verizon Data Breach Report 2021, in 2020 real-time security incidents were detected, …
Wi-Fi and its relationship with the zero-trust model
Zero-trust network architecture (ZTNA) provides a holistic view of business cybersecurity that secures your applications and environment when accessed by any user, device, or location. A comprehensive zero-trust model enables you to mitigate, detect and respond to threats. Adopting ZTNA brings significant benefits to businesses it supports rapid Cloud adoption and user security, which is …
9 Reasons to Use a Corporate Password Manager
Teaching about password security in the early 2000s would generally start with a question to the audience how many of you have up to 10 passwords to remember? How about 25? Anyone with further than 50? The moment I generally start with “ how many credentials do you believe to have still active? Lower than …
What Is Ransomcloud?
Tech decision makers surveyed by Pulse admitted last time that nearly 3 out of 4 companies (71%) endured a ransomware incident and at least 12 of these incidents involved payments. This shows that ransomware attacks are proving to be a economic business for vicious cyber actors as they constantly put associations’ cybersecurity measures to the …
The Game Changer to Qualify for Cyber Insurance
MFA is a must-have if you are looking to purchase cyber insurance for your business Recent cybersecurity incidents and ransomware attacks have increased, driving companies to apply for cyber insurance. When doing so, companies have been facing one newpre-requisite to come eligible multi-factor authentication protection of your users and assets. How to get started when …
WatchGuard Trusted Wireless Environment
Don’t Let Wi-Fi Be Your Biggest Security Gap In 2017, there were 8.4 billion associated gadgets and the volume is relied upon to hit 20.4 billion by 2020, as per investigator firm Gartner. Programmers like to pursue the point of failure in the security chain and it doesn’t take a lot to hack into the …
WatchGuard Resources to Aid with Remote Worker Security
Are you looking for quick and effective ways to increase remote worker security? These steps can improve work continuity and cybersecurity. Scrutinize your business’s plan to continue operations while employees are out of the office Revise policies to communicate expectations for remote and mobile workers Teach employees how to avoid falling victim to cybersecurity attacks …
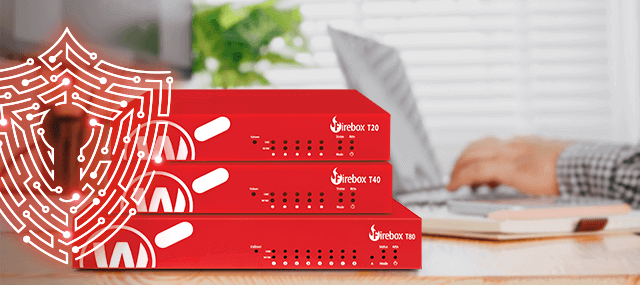
WatchGuard releases three new Firebox T Series UTM appliances
WatchGuard is happy to announce the discharge of three new Firebox T Series UTM appliances: Firebox T20, T40, and T80. These latest Firebox models provide an upgrade path for our existing Firebox T Series customers and offer faster processors and more memory. Delivering big security during a small appliance, each WatchGuard Firebox includes an entire …